
This is a small page that tries to bring awareness of the risks that allowing Docker daemon to listen on localhost without TLS enabled. i.e.: using flags like "-H localhost:2375" or ticking the box in the Docker settings. This page is deployed on http://docker-check.aitorpazos.es to be able to reach the Docker daemon without using TLS. Otherwise, the mixed content policies in your browser will block reaching HTTP sites from a HTTPS page.
You can check the code at https://github.com/aitorpazos/aitorpazos.github.io
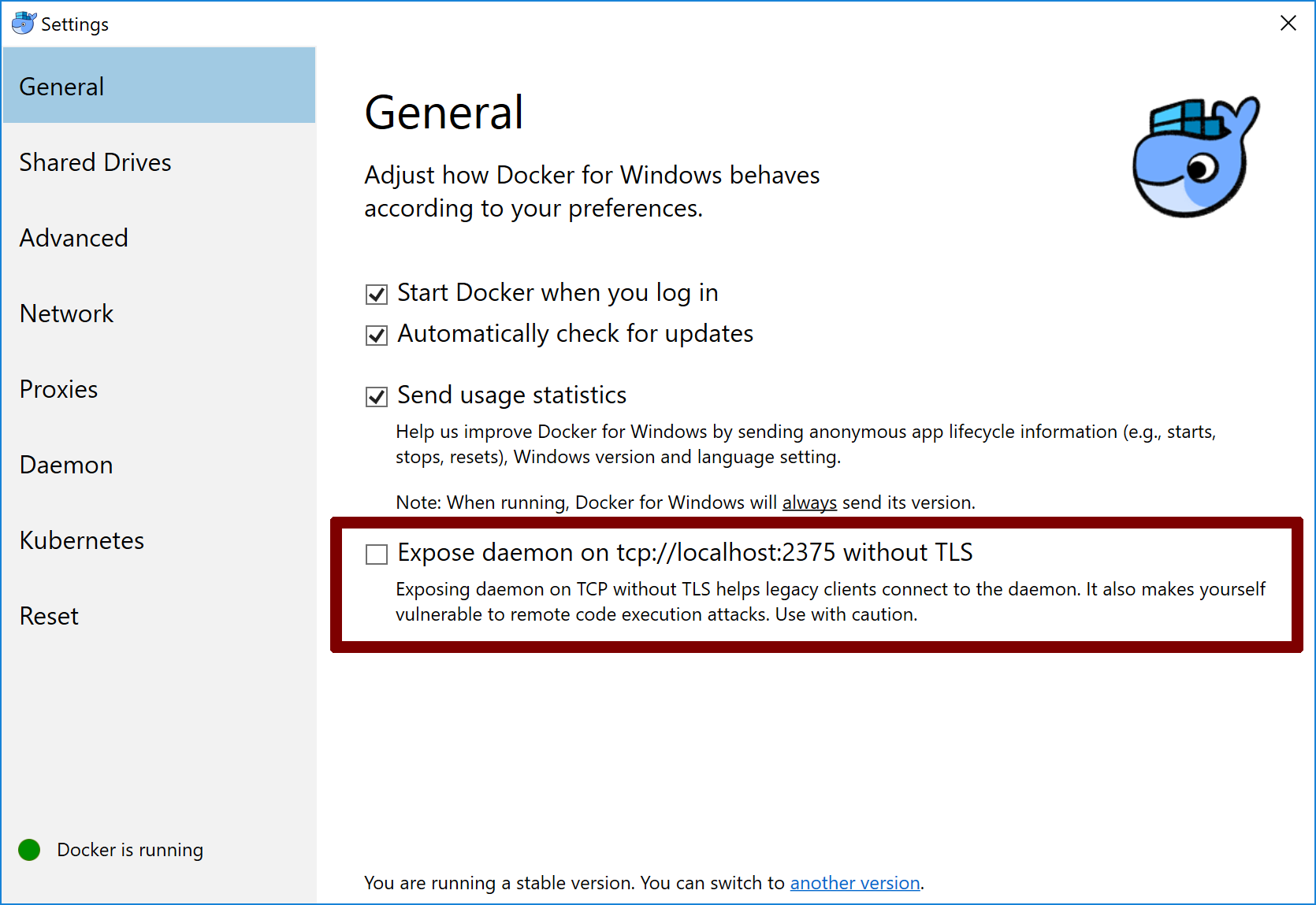
The docker daemon is exposed using the loopback interface (i.e.: tcp://localhost:2375), which limits greatly the harm that can be done using it. However, this setting leaves the docker daemon more easily addressable by potential bad actors.

Your browser's same-origin policy mechanisms (https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy) is the only barrier that prevents an evil site to run any command on your machine, which is not a situation you want to be in.
These are examples of read-only operations that same-origin protections prevents (this is shown as green).
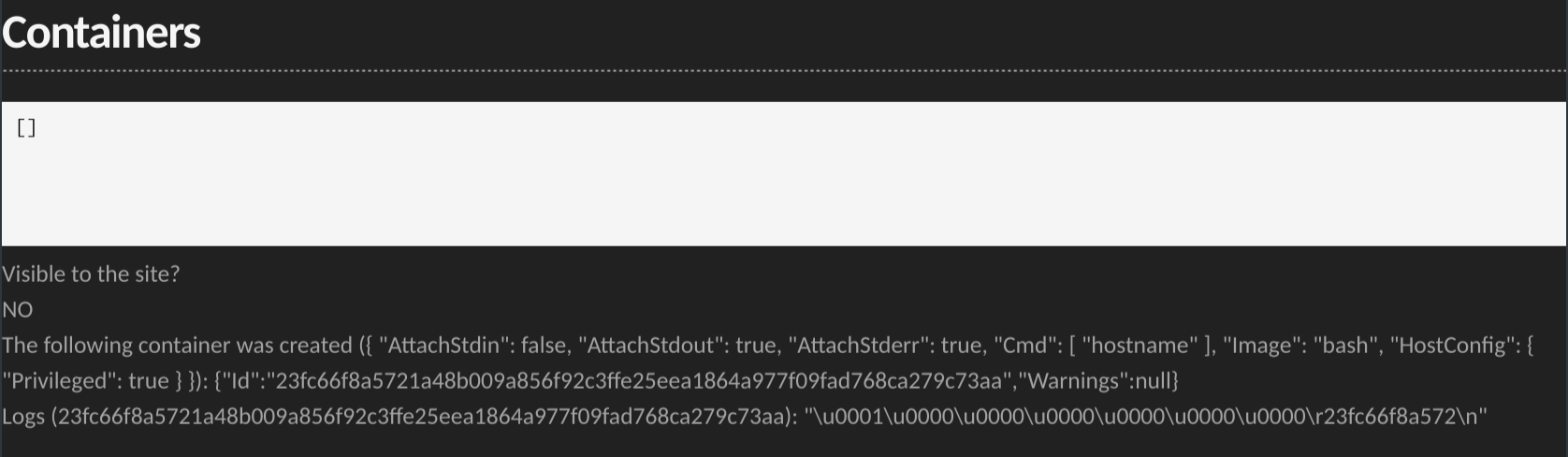
For example, in the containers section, in my very restricted tests I've already noticed that, the KDE's Falkon browser is failing to enforce that policy as it should, allowing a site to run containers.
An additional protection is that the attacker must use HTTP sites as browsers will refuse to load mixed content (perform HTTP requests from HTTPS sites).
On the left a well-behaved browser, on the right, a misbehaving one:


If you see a broken page below chances are that you are not running docker at all or you haven't enabled it to listen on port 2375. That is good :)
If you see a long text string, then your Docker daemon is listening on port 2375 without requiring authentication and I'd recommend that you double check if you really need this.
Request to the docker daemon:
This actions can be triggered by yourself clicking on those buttons.
However, to demonstrate how this can be leveraged in an automated fashion by bad actors, you can see how this can be triggered automatically by appending "?timer=number_of_milliseconds_to_trigger_actions" (e.g.: "?timer=5000")